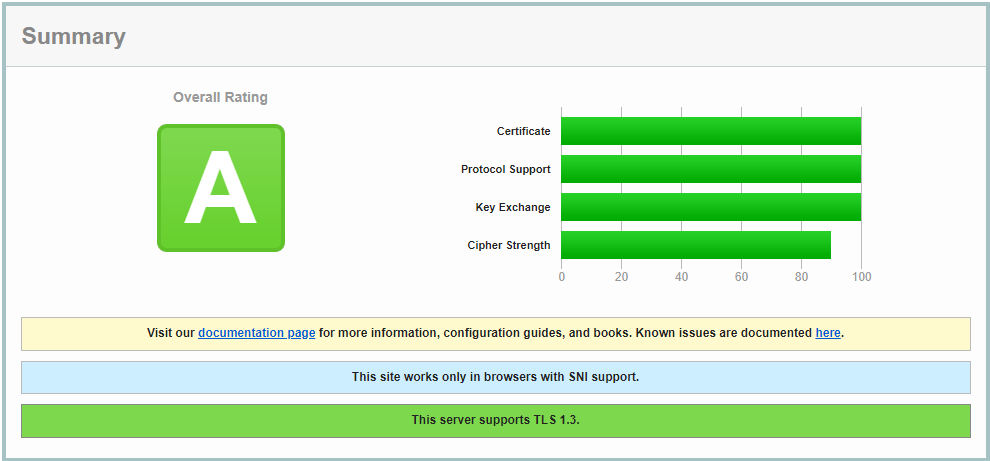
Voici les différents fichiers de configuration pour créer un conteneur Traefik permettant d'obtenir une très bonne note sur le site ssllabs
¶ Prérequis
- Avoir installé docker et docker compose sur un serveur
- Avoir un certificat let's encrypt
- Avoir créé les fichiers nécessaires selon l'arborescence suivante
/répertoire
|--------- docker-compose.yml
|--------- traefik.yml
|--------- Config
|--------- config.yml
|--------- tls.yml
¶ docker-compose.yml
version: "3.8"
services:
traefik:
image: traefik:latest
networks:
- traefik-network
restart: always
## Optionnel : supprimer cette ligne et les commentaires seulement si le conteneur Autoheal est utilisé
# healthcheck:
# test: grep -qr "traefik" /proc/*/status || exit 1
# interval: 1m
# timeout: 30s
# retries: 3
ports:
- 80:80
- 443:443
volumes:
- /etc/localtime:/etc/localtime:ro
- /var/run/docker.sock:/var/run/docker.sock:ro
- /****/traefik/traefik.yml:/etc/traefik/traefik.yml:ro # mettre le chemin exacte
- /****/traefik/config/:/etc/traefik/config/:ro # mettre le chemin exacte
- /etc/letsencrypt/********/******/:/certs:ro # mettre ici le chemin complet du répertoire contenant le certificat
deploy:
resources:
limits:
memory: 512M
labels:
# - autoheal=true # Optionnel : supprimer ce message et le commentaire en début de ligne seulement si le conteneur Autoheal est utilisé
- traefik.enable=true
- traefik.docker.network=traefik-network
- traefik.http.routers.traefik.entrypoints=http
- traefik.http.routers.traefik.rule=Host(`proxy.******.**`) # mettre le ndd
- traefik.http.middlewares.traefik-auth.basicauth.users=*****:******************** # mettre ici le user:hash_du_password
- traefik.http.middlewares.traefik-https-redirect.redirectscheme.scheme=https
- traefik.http.routers.traefik.middlewares=traefik-https-redirect
- traefik.http.routers.traefik-secure.entrypoints=https
- traefik.http.routers.traefik-secure.rule=Host(`proxy.******.**`) # mettre le ndd
- traefik.http.routers.traefik-secure.middlewares=traefik-auth
- traefik.http.routers.traefik-secure.tls=true
- traefik.http.routers.traefik-secure.service=api@internal
- traefik.http.services.traefik.loadbalancer.server.port=8080
networks:
traefik-network:
external: true
¶ traefik.yml
## CONFIGURATION STATIQUE POUR TRAEFIK ##
global:
checkNewVersion: false
sendAnonymousUsage: false
log:
level: INFO
format: common
api:
insecure: false
dashboard: true
entryPoints:
http:
address: ":80"
https:
address: ":443"
providers:
docker:
endpoint: "unix:///var/run/docker.sock"
watch: true
exposedByDefault: false
swarmMode: false
file:
directory: /etc/traefik/config/
watch: true
¶ Contenu du répertoire “Config”
¶ config.yml
http:
middlewares:
https-redirect:
redirectScheme:
scheme: https
hsts-headers:
headers:
frameDeny: true
sslRedirect: true
browserXssFilter: true
contentTypeNosniff: true
stsIncludeSubdomains: true
stsPreload: true
stsSeconds: 31536000
forceStsHeader: true
referrerPolicy: same-origin
customResponseHeaders:
permissions-Policy: vibrate=(self), geolocation=(self), midi=(self), notifications=(self), push=(self), microphone=(), $
X-Permitted-Cross-Domain-Policies: none
expect-ct: max-age=604800, report-uri="https://oak.ct.letsencrypt.org/2021"
¶ tls.yml
# Dynamic configuration
tls:
options:
default:
minVersion: VersionTLS12
sniStrict: true
cipherSuites:
- TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 # TLS 1.2
- TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305 # TLS 1.2
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 # TLS 1.2
- TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305 # TLS 1.2
- TLS_AES_256_GCM_SHA384 # TLS 1.3
- TLS_CHACHA20_POLY1305_SHA256 # TLS 1.3
- TLS_FALLBACK_SCSV # TLS FALLBACK
curvePreferences:
- secp521r1
- secp384r1
modern:
minVersion: VersionTLS13
# Comment below if not using own certificate
certificates:
- certFile: "/certs/fullchain1.pem" #certificate path in the container
keyfile: "/certs/privkey1.pem" #private key path in the container
stores:
- default
stores:
default:
defaultCertificate:
certFile: "/certs/fullchain1.pem" #certificate path in the container
keyFile: "/certs/privkey1.pem" #private key path in the container
¶ Résultat sur ssllabs :